For many, the holiday season is defined by time spent with loved ones, goodwill, and giving.
'Tis is also the time for cybercriminals to be plotting to steal Christmas.

As retailers rollout their holiday sales, nefarious actors look forward to snaring thousands of online shoppers with bogus sites, fake social media campaigns, and emails impersonating real brands. These "spoofing" sites and fake messages are designed to entice consumers to spend money on products that they will never receive. These actors are also apt to find victims through other means, including charity and travel scams.
Non-payment or non-delivery scams cost people more than $0 million in 2021 (IC3 report)
Tips for Shoppers to Prevent Theft and Fraud
DON'T click on any suspicious links or attachments in emails, or on websites and social media. These links compromise your information, such as your name, password, and bank account number. This includes requests from companies asking you to update your account. Additionally, you may unknowingly download harmful malware to your device by clicking on these corrupted links.
For each site you plan to order from or donate toward, check to see that the URL is secure and genuine. Optimize a website reputation check, such as URLVOID. Do research and check to see if there are reviews available, avoid businesses or charities with no ratings at all. If you are really wary of a website, look up a business phone number and call them.
Use a credit card while shopping online and regularly check your bank statements for suspicious activities. Remember to NEVER wire money directly to a seller. Verify the charge with the intended recipient, verify that email address are valid. We also advise against using pre-paid gift cards to purchase items as well.
Once you make a purchase, always record the tracking number so you can track the delivery process.
Learn to identity the red flags and remain vigilant during the season of giving, let's examine the number of creative ways that criminals are manipulating buyers and sellers worldwide.
Business and email compromise
Business email compromise (BEC) and email account compromise (EAC) are elaborate scams aimed at businesses and individuals performing money transfers. While the scams used to involve simple hacking, it has evolved into a much more sophisticated scheme, compromising legitimate business email accounts through tech intrusion techniques to perform unauthorized transfers of funds.

In the past, actors had simply spoofed business accounts. Now fraudsters are optimizing virtual meetings to hack emails and will act as business leaders to instigate fraudulent wire transfers. Often these wire transfers are converted into crypto wallets and are ultimately deposited into anonymous crypto wallets, making tracing extremely difficult for authorities.
Ransomware
Ransomware is an invasive software, or malware, that encrypts unwanted data on a computer, making it unusable. Cyber criminals will withhold the data until a handsome ransom is paid. If the ransom is not paid, the victim’s data remains untouchable.
$0M
lost in 2021, with 3,729 complaints identified with ransomware documented by the IC3

These criminals are willing to go through great efforts to pressure and intimidate victims into paying their fee, and will threaten to destroy the sensitive data or to release it to the public.
Steps to take against Ransomware
Having an outdated operating system puts you at risk not only for business disruptions and system failure, but prime for a cyber attack or security breach as well. Think of it as leaving your back door unlocked. Keep your system safe by regularly updating and upgrading.
Train your staff to properly identity, avoid, and respond to the signs of a ransomware attack. Even the most sophisticated networks could be vulnerable to an attack if an untrained eye clicks a suspicious link or mistakenly opens an infected attachment. Make it easier for your employees to do the right thing rather than make a mistake.
Back up your data early and often. It is your best line of defense against ransomware attacks. Organizations and individuals who have sufficient offline backup can restore their data and operations without paying the ransom money. However, it is crucial to understand that backups alone don’t ease the restoration process or mitigate extortion tactics. The best solution is to prevent the initial breach.
Tech support fraud
This holiday season, fraudsters will be posing as customer, security, or technical support roles with well-known tech companies, with the intent to defraud individuals.

Victims are deceived by these bad actors into giving away their valuable personal information, and many report being instructed to make wire transfers to overseas accounts or to purchase large amounts of prepaid cards.
Most victims of tech fraud, almost 0%, report to be over 60 years old
The elderly are notoriously targeted by these criminals and they experience at least 68% of the total losses of tech fraud costs (almost $238 million). You can report any fraud targeting older people to the Federal Trade Commission online or at 877-382-4357.
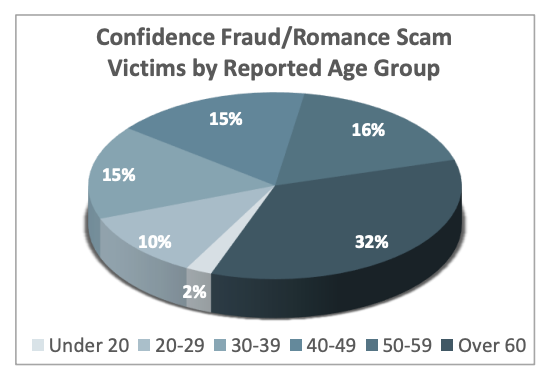
Confidence fraud and romantic scams
These are scams aimed to "tug at one's heartstrings," taking advantage of people's emotions, only to ultimately empty their pockets.
0
victim reports collected by the IC3 in 2021
Con artists are prevalent on most dating and social media channels, adopting an identity to prey on victims, hoping to gain affection and trust. Last year, thousands of reports were taken by the IC3, who received thousands of complaints from victims of online relationships resulting in sextortion or investment scams.

These charming, persuasive con artists weasel their way into people's lives quickly and effectively. These scams are time-tested and heavily-scripted, with the intent to establish a romantic relationship as quickly as possible. There may even be a marriage proposal and plans made to meet in person, but that will never happen. However, eventually, these actors will ask for money.
More than $0 million in losses to confidence/romance scams in 2021
Grandparents also fall into this category. Grandparent scams are when criminals impersonate a panicked loved one and claim to be in trouble, pleading for money immediately. These actors are knowledgable, obtaining pieces of information from the social media accounts of family members, using details as leverage.
Charity fraud schemes seek out donations for organizations that do little or no work, instead the funds are transferred to the fake charity's creator. While these scams could happen at any time during the year, folks tend to be most charitable during the holiday season, and scammers are looking to take advantage of people's goodwill.
To check the validity of a charity, check out organization CharityWatch or follow the advice provided by the Federal Trade Commission.
Cryptocurrency
Among the 2021 complaints received by the IC3, ransomware, business e-mail compromise (BEC) schemes, and the criminal use of cryptocurrency where the top incidents reported. In fact, con artists had a landmark year, the IC3 received a record number of 847,376 complaints.
0
complaints recorded involving cryptocurrency (IC3 report)
While that number showed a decrease from 2020’s crypto victim count (35,229), the loss amount reported in IC3 complaints increased nearly seven-fold, from 2020’s reported amount of $246,212,432, to total reported losses in 2021 of more than $1.6 billion.
Record losses exceeding $0 billion, a 7% increase from 2020 (IC3 report)

Global cybercrime costs are expected to grow by 0% per year over the next five years
The most proactive solution against this overwhelming threat is to prevent an attack in the first place. Identomat's AI-generated end-to-end verification solution has helped a number of businesses upscale their KYC and AML routine and helped them achieve success.
If something is too good to be true, it likely is.

The holiday season is not only a hectic time for your business, but it is a bustling time for cybercriminals too. Cyber incidents are absolutely crimes deserving of an investigation, leading to judicial repercussions for the perpetrators who commit them. When in doubt, remember the golden rule of the Internet...